Planning The Physical Network
When planning out a network, whether for a small home office, or for enterprise businesses, you need to consider various different factors: Expected number of users, Static or Dynamic WAN or LAN routing, Security, site to site connectivity, remote access, public access, storage, privacy, and services you will be running/providing internally. You also want to think about scalability and a bit of future proofing. I would be remiss if I did not mention that in the small business and enterprise space, you should also consider failover, diversity, and disaster recovery.
At my job I have a mentor (former manager) that always told me that solution engineering is an “art”. In other words, everyone will paint the picture a different way. Some will think some solutions are better than others, and they might be, but sometimes we can simply accomplish the same end goal in different ways. Regardless, the network devices and transport is the foundation of your network environment. You will build everything on top of this and getting this piece at least MOSTLY right is imperative.
I will be posting a series of blogs about my network, the tools I use (almost all open source), that have helped me design solutions and understand new technologies, hardware, and network services. First though, we will walk through the following list below regarding the physical set up of my network, connectivity, and security. Maybe it will give you some ideas.
Transport and CPE
For a home office like mine, it would be reasonable to assume that all I needed was an internet connection and router with a stateful firewall. However, I wanted to do a bit more like host my own media service accessible outside the network, be able to access files from my own “cloud” server, and I wanted the ability to separate my work, home, and guest networks so there was not risk of security on my home or work network.
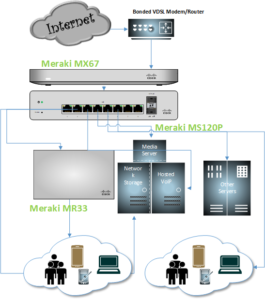
As you can see from the simple diagram here, I have some normal components for a home and then a not so normal Meraki SDWAN Security Stack with an enterprise class wireless access point. Working as a Solutions Engineer with a tier 1 telecom service provider I had the opportunity to complete my CMNA and in partnership with my company, Cisco provided me with this stack and a license to demo. The best way to demo is to use it everyday, and I do. It has allowed me to know this product in and out and be able to lead with the Meraki line for various solutions. I don’t expect you to pay for a stack like this in a small home or office, but the concept would still be the same. Even if you use your internet service providers modem for routing, DNS, etc. , use a NGFW (security device) or a cloud based security service to secure you internet traffic.
If not Meraki, what devices would I recommend? Unify by Ubiquiti. They offer the same style of stack equipment and very reasonable cost.
So here is how it is set up. My WAN transport is a bonded VDSL highspeed internet connection from the local phone company. I went with bonded DSL as it was the only way I could get faster speeds in the area I am in. I ended up with a 60Mbps down/5Mbps up internet circuit. I have that copper circuit home run directly to my network closet where it terminates to the provided DSL modem/router (Zyxel C3000z). Because this is a bonded DSL line (2 copper pairs), I have to rely on the services providers modem to combine the 2 signals. Other than that I have no need for that equipment so I set the router to bridge mode.
The C3000z (gateway) then provides internet service to my Meraki MX64 Security/SDWAN device. I will get into some of the configurations on this later, but this device is being given a DHCP IP from the gateway. Most providers will be able to provide you with a static IP for an additional cost ($15 dollars for a /30 from my provider), but with Dynamic DNS and scripting, there really is no need. external services can use dynamic DNS to connect and you should proxy your IP Address anyway and can use Dynamic DNS with providers such as DuckDNS or Cloudflare. I will cover dynamic DNS with both of these services in later posts, but the MX64 does provide a dynamic DNS with the cloud controller from Cisco and I am using that for VPN access…. more to come on that as well 🙂
NGINX is a free, open-source, high-performance HTTP server, reverse proxy, and IMAP/POP3 proxy server. NGINX is known for its high performance and stability. Free SSL with Let’s Encrypt. Perfect for home networks. NGINX has a rich feature set, simple configuration, and low resource consumption. NGINX scales in all directions.
Cisco Meraki - SDWAN
The Meraki MX64 is a enterprise security appliance designed for distributed deployments that require remote administration. It is ideal for network administrators who demand both ease of deployment and a state-of-the-art feature set. The Meraki Dashboard allows for simple and easy deployment with minimal pre-configuration in almost any location. The MX64 is also available in a Wireless model that can provide 802.11ac coverage for wireless clients. I am not using a wireless model.

The MX64 provides a 1G Ethernet connection to a Meraki MS120 Power over Ethernet Switch. This is an 8 port switch. Although the MX64 has additional ports to be used (avoiding a single point of failure using just the switch), I am utilizing the POE from the MS120P to power many of my devices and it sits in a really convenient spot in my rack. Being it’s a small home office, I’m ok with the risk, my work isn’t that important 🙂 For wireless access in my SoHo, I am using a Meraki MR36
The MR36 is a cloud-managed 2×2:2 802.11ax access point that is designed for next-generation deployments in offices, schools, hospitals, shops, and hotels, the MR36 offers high throughput, enterprise-grade security, and simple cloud management.
The MR36 provides a maximum of 1.7 Gbps aggregate frame rate with concurrent 2.4 GHz and 5 GHz radios. A dedicated third radio provides real-time WIDS/WIPS with automated RF optimization, and a fourth integrated radio delivers Bluetooth scanning and beaconing.

I am using multiple different SSID Networks to segment my home network. This includes separate networks where I can route specific traffic to specific destinations by user group, shape traffic by SSID, and apply QoS.
One of the coolest features of the Meraki line is the SD-WAN component, which allow for low-cost WAN links that help reduce the high costs of MPLS circuits and created a private WAN network. it should be noted that SD-WAN is not intended to be a MPLS killer … but that’s another blog. I only have my home office that I need connectivity for, so I will not be able to take advantage of these features. However, I do still use the VPN client to reach my private network.
OpenDNS - Security Configuration
The topic of security has become a big concern. Newscasts have shared how vulnerable networks have become targets of hackers and ransomware plots. Not just large companies, but Individuals have been targets of these attacks as well; although, admittedly by different targeting means (email, RDP attacks, etc.).
So where do people like myself in a SoHo environment fit it to the mix of security and how do we protect ourselves? Again, to me, this process is an “art” and there are many ways to take preventative measures, but do not break the bank to do it. calculate your risks, ask in forums, as a friend in the industry. I wont share every security method I am taking in this post (I will have subsequent posts), but I will stress that if you have a domain or any IP Services pointing toward your home network, you must secure your public network environment with more than just the provided stateful firewall in your ISP’s modem/router and look at protecting your anyomitity and PII by using a secure DNS provider -this should be free.
Securing my network, I use IDS/IPS protection and firewall via my Meraki Security Device, A VPN Client for private network access, A VPN provider with ad blocking for internet use (Surfshark), Cloudfare for poxy, SSL, DDOS and Bot mitigation, NGINX Proxy Manager, and OpenDNS which masks name resolution from my ISP and automatically filters known phishing websites that try to steal your identity and login information by pretending to be a legitimate website.
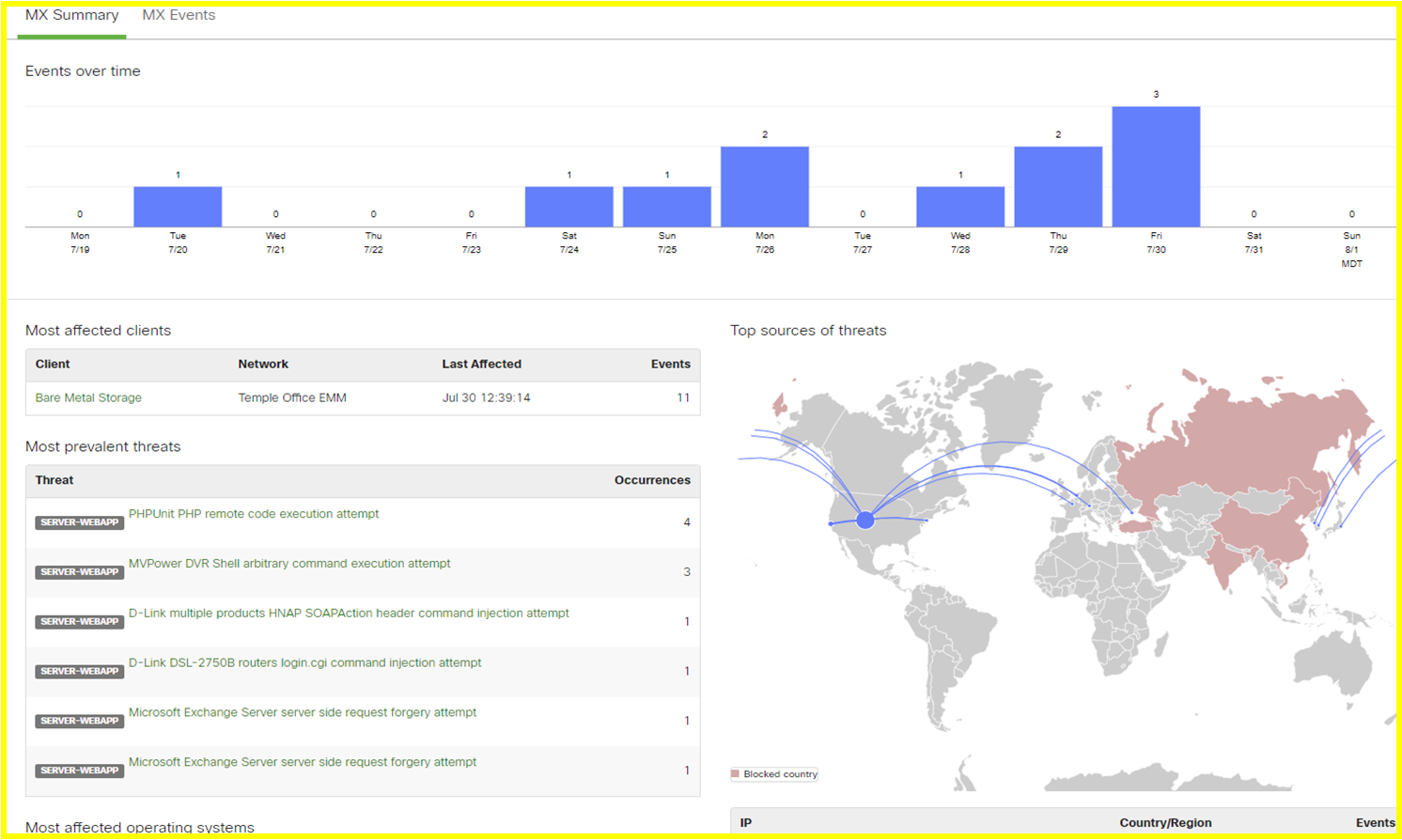
Once I pointed a public IP toward my network, I started seeing threats right away. My Meraki MX Security Device was reporting threat mitigation from threats, and through the device I was able to block regions I did not care to sent traffic to or receive from:
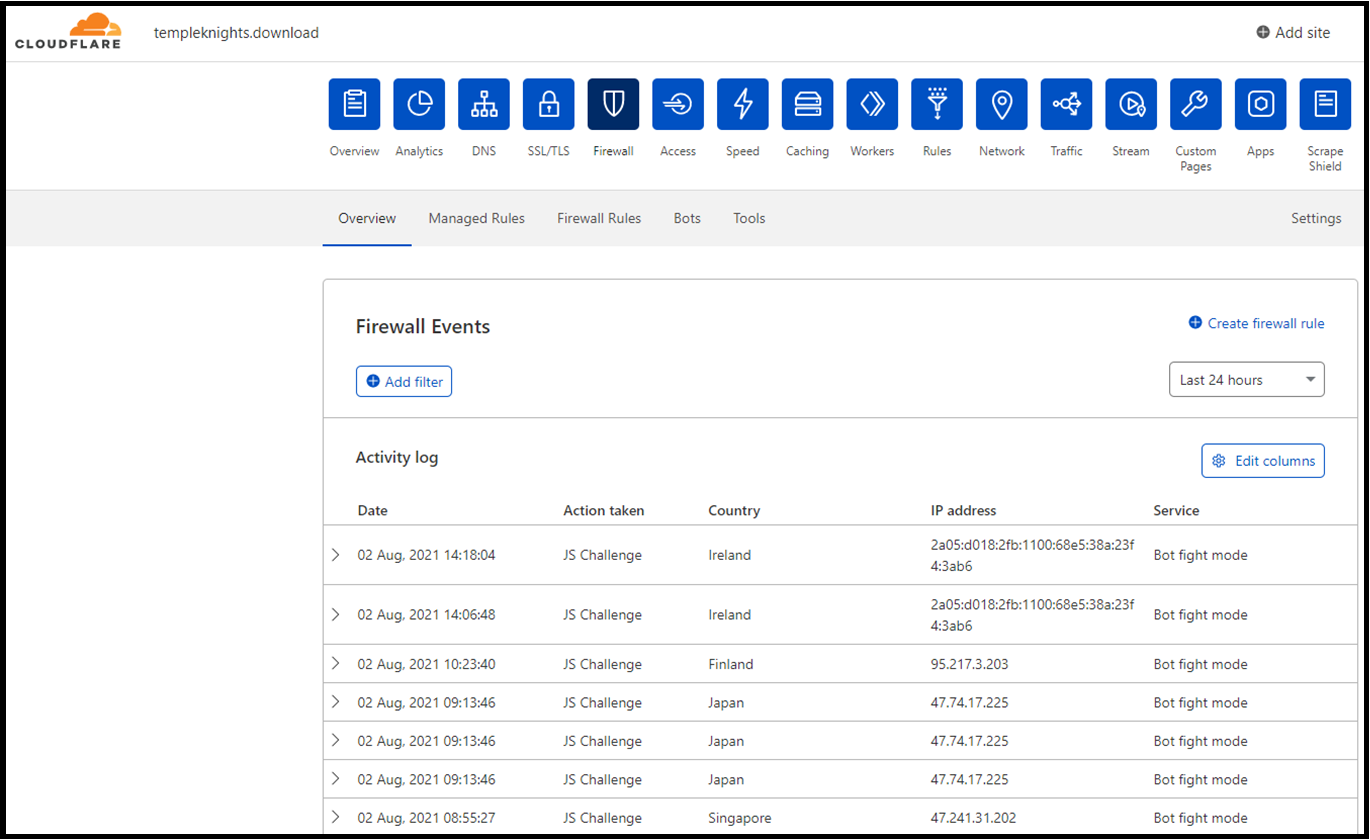
 Cloudfare (free tier) was also working to mitigate threats as well and analytics from the same time from show they were blocking threats before the MX was catching roll over attacks.
Cloudfare (free tier) was also working to mitigate threats as well and analytics from the same time from show they were blocking threats before the MX was catching roll over attacks.
OpenDNS also provides similar reporting if you use their Home or Free user tier, but you can also just configure OpenDNS nameservers in your gateway to utilize the service:
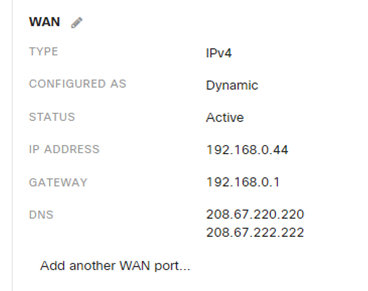
So why care about OpenDNS? Well most people use the DNS name servers provided by their ISP as it is pre-configured, an most users don’t care as long as it works. That means your provider has a whole lot of people asking them the resolve web names into IP Addresses! Using a DNS server from another provider can speed up your service and provide anonymity from your ISP on what sites you’re visiting. OpenDNS is not your service provider, so the only identifiable data is a dynamic IP address that they cannot relate to an ISPs consumer base that is not theirs. Additionally, with customizable filtering categories, you are in control of what websites are visited from your network. Finally, OpenDNS will proactively block phishing websites that try to steal your identity and login information. DNS is just one step in considering privacy and as another tool that is overlooked often for security.